In today's digital world, mobile devices are essential for many operations, serving as tools for communication, collaboration and productivity. The need for strong Mobile Device Management (MDM) security is crucial.
As businesses increase their use of mobile technology to streamline operations and optimize employee productivity, it’s important to prioritize data security to protect against cyber threats.
Why Is MDM Security Critical?
The Importance of MDM Solutions
Mobile Device Management helps organizations manage and secure mobile devices that are connected to their networks.
With more mobile devices in the workplace, effective security practices are a must. MDM helps to maintain data protection, enforce compliance policies and mitigate security risks.
Implementing an MDM solution allows businesses to control device configurations and remotely manage access permissions. You can do this without leaving your desk or having the device in hand. It also helps to reduce the likelihood of data breaches and minimizes unauthorized access.
Why MDM Security Is Paramount
Bring Your Own Device (BYOD) policies are being adopted by more businesses. As more employees use their personal devices for work tasks, strong Mobile Device Management security is critical for everyday operations.
With a wide array of devices and operating systems accessing corporate resources, organizations face the challenge of ensuring uniform security standards across many platforms.
MDM security solutions address this challenge by providing cross-platform and centralized management capabilities. This allows IT administrators to enforce security policies consistently across all devices, regardless of their make or model.
What Is MDM Security?
At its core, Mobile Device Management security is a range of features and functionalities that focus on cybersecurity.
These features include device monitoring, data encryption, remote wipe capabilities, application management and compliance policies. By implementing these security measures, organizations can safeguard against malware threats, enforce access controls and ensure compliance with regulatory requirements.
Click to expand and download
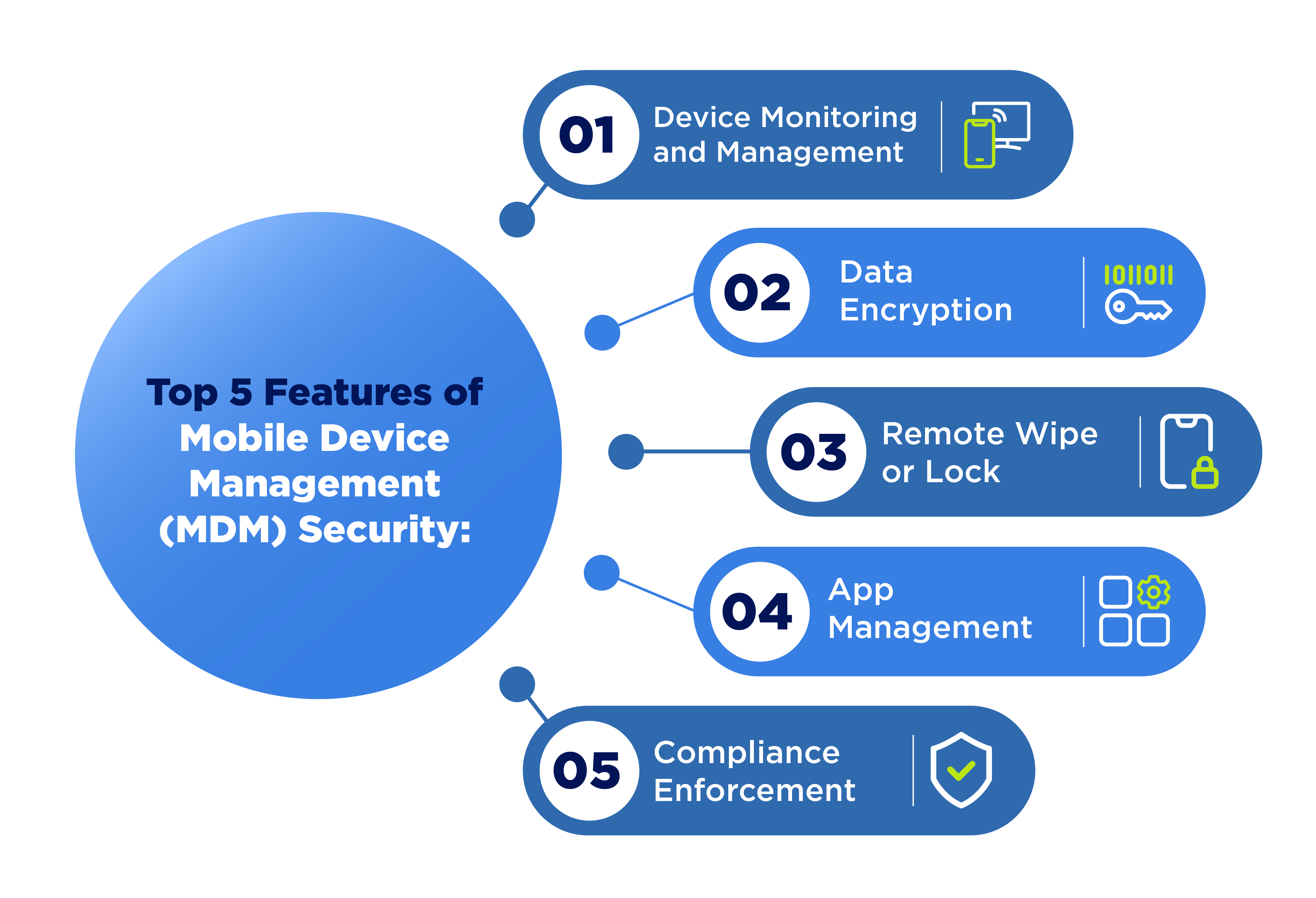
Top 5 Features of Mobile Device Management (MDM) Security:
1. Device Monitoring and Management
Allows businesses to remotely monitor and manage mobile devices, including configuration, updating and enforcing security policies.
2. Data Encryption
Ensures that data stored on mobile devices is encrypted, protecting it from unauthorized access in the event of loss or theft.
3. Remote Wipe/Lock
Enables administrators to remotely wipe or lock a device in case it is lost or stolen, preventing unauthorized access to sensitive data.
4. App Management
Allows businesses to control which apps can be installed and run on mobile devices, reducing the risk of malware and unauthorized software usage.
5. Compliance Enforcement
Helps ensure that mobile devices comply with organizational security policies and regulatory requirements, such as password complexity, device encryption and software updates.
Business can leverage insightful monitoring and reporting capabilities to proactively identify and address security concerns before they escalate into full-blown breaches.
The Role of MDM Security in Comprehensive Security Strategies
Guarding the Gateways: MDM's Vital Role in Security
Mobile devices serve as the primary endpoints for accessing corporate networks and resources. Mobile Device Management security plays a pivotal role in guarding the gateways to enterprise infrastructure.
Implementing strong authentication rules, encryption protocols and access controls is crucial. MDM solutions help protect against data exfiltration.
Organizations can detect and respond to security incidents in real-time by monitoring device activity and network traffic remotely, minimizing the impact of potential breaches.
Strengthening the Perimeter: MDM Security's Contribution
Mobile security also contributes to strengthening the perimeter defenses against external threats. By implementing advanced threat detection and prevention mechanisms, organizations can find and prevent problems before they negatively impact their systems.
Furthermore, by integrating security, businesses can achieve greater visibility and control over their digital assets, ensuring protection against cyber threats such as ransomware.
Integrated Defense: MDM Security and Holistic Protection
Effective Mobile Device Management security is not just about safeguarding individual devices or endpoints.
The term "security posture" refers to an organization's overall approach and readiness toward security. Having a security posture connected to the entire business is also important.
Integrating MDM solutions with network firewalls, secure web gateways and other systems can allow organizations to develop a detailed defense strategy. This comprehensive approach addresses various aspects of security, safeguarding against a wide range of potential risks.
By leveraging insightful monitoring and reporting capabilities, businesses can gain intelligence into emerging security trends and patterns. This will allow them to proactively adapt their security strategies.
Preventive Measures in MDM Security
In the ever-evolving landscape of cybersecurity threats, staying one step ahead of challengers is essential. Mobile Device Management security means implementing strong access controls, enforcing encryption standards and regularly updating device configurations to address known weaknesses.
Educating employees about security best practices and conducting regular security audits help minimize breaches and ensure compliance. These proactive measures enhance overall security and reduce risks.
Trends and Innovations in MDM Security
As technology advances, the field of Mobile Device Management security is evolving with new challenges and opportunities. Trends such as zero-trust security, AI-based threat detection and blockchain for identity management are transforming enterprise security.
These trends improve MDM solutions and make business operations safer.
The increasing number of Internet of Things devices and the arrival of 5G connectivity will lead to a wider and more intricate security landscape. This will require ongoing innovation and adaptation to keep up with evolving threats.
Advice for the Future
To keep enterprise networks and assets safe in this dynamic digital environment, MDM security monitoring and reporting should remain top of mind.
Businesses need to stay informed about emerging trends and continually adapt their security strategies to mitigate risks, protect sensitive data and ensure compliance.